This is the tool I used sometimes to recover passwords that I have forgotten. I do not encourage hacking. This tool is actually considered a backdoor sometimes by some of the security software in the market. Personally I think it is useful, but people tend to abuse it.
Cain & Abel is a password recovery tool for Microsoft Operating Systems. It allows easy recovery of various kind of passwords by sniffing the network, cracking encrypted passwords using Dictionary, Brute-Force and Cryptanalysis attacks, recording VoIP conversations, decoding scrambled passwords, recovering wireless network keys, revealing password boxes, uncovering cached passwords and analyzing routing protocols.
Cain & Abel has been developed in the hope that it will be useful for network administrators, teachers, security consultants/professionals, forensic staff, security software vendors, professional penetration tester and everyone else that plans to use it for ethical reasons.
The tool is divided into 2, namely Cain, and Abel.
Cain’s features
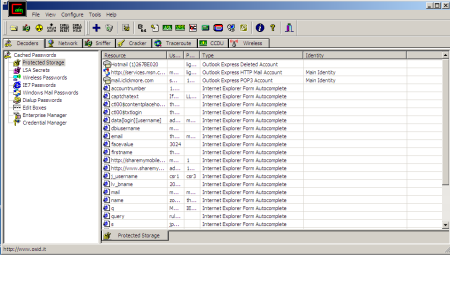
- Protected Storage Password Manager
Reveals locally stored passwords of Outlook, Outlook Express, Outlook Express Identities, Outlook 2002, Internet Explorer and MSN Explorer. - Credential Manager Password Decoder
Reveals passwords stored in Enterprise and Local Credential Sets on Windows XP/2003. - LSA Secrets Dumper
Dumps the contents of the Local Security Authority Secrets. - Dialup Password Decoder
Reveals passwords stored by Windows “Dial-Up Networking” component. - APR (ARP Poison Routing)
Enables sniffing on switched networks and Man-in-the-Middle attacks. - Route Table Manager
Provides the same functionality of the Windows tool “route.exe” with a GUI front-end. - SID Scanner
Extracts user names associated to Security Identifiers (SIDs) on a remote system. - Network Enumerator
Retrieves, where possible, the user names, groups, shares, and services running on a machine. - Service Manager
Allows you to stop, start, pause/continue or remove a service. - Sniffer
Captures passwords, hashes and authentication information while they are transmitted on the network. Includes several filters for application specific authentications and routing protocols. The VoIP filter enables the capture of voice conversations transmitted with the SIP/RTP protocol saved later as WAV files. - Routing Protocol Monitors
Monitors messages from various routing protocols (HSRP, VRRP, RIPv1, RIPv2, EIGRP, OSPF) to capture authentications and shared route tables. - Full RDP sessions sniffer for APR (APR-RDP)
Allows you to capture all data sent in a Remote Desktop Protocol (RDP) session on the network. Provides interception of keystrokes activity client-side. - Full SSH-1 sessions sniffer for APR (APR-SSH-1)
Allows you to capture all data sent in a HTTPS session on the network. - Full HTTPS sessions sniffer for APR (APR-HTTPS)
Allows you to capture all data sent in a HTTPS session on the network. - Certificates Collector
Grab certificates from HTTPS web sites and prepares them to be used by APR-HTTPS. - MAC Address Scanner with OUI fingerprint
Using OUI fingerprint, this makes an informed guess about what type of device the MAC address from. - Promiscuous-mode Scanner based on ARP packets
Identifies sniffers and network Intrusion Detection systems present on the LAN. - Wireless Scanner
Can scan for wireless networks signal within range, giving details on its MAC address, when it was last seen, the guessed vendor, signal strength, the name of the network (SSID), whether it has WEP or not (note WPA encrypted networks will show up as WEPed), whether the network is an Ad-Hoc network or Infrastructure, what channel the network is operating at and at what speed the network is operating (e.g. 11Mbps). Passive scanning and WEP IVs sniffing are also supported using the AirpCap adapter from CACE Technologies. - 802.11 Capture Files Decoder
Decode 802.11 capture files (wireshark, pcap) containing wireless frames encrypted with WEP or WPA-PSK. - Access (9x/2000/XP) Database Passwords Decoder
Decodes the stored encrypted passwords for Microsoft Access Database files. - Base64 Password Decoder
Decodes Base64 encoded strings. - Cisco Type-7 Password Decoder
Decodes Cisco Type-7 passwords used in router and switches configuration files. - Cisco VPN Client Password Decoder
Decodes Cisco VPN Client passwords stored in connection profiles (*.pcf). - VNC Password Decoder
Decodes encrypted VNC passwords from the registry. - Enterprise Manager Password Decoder
Decodes passwords used by Microsoft SQL Server Enterprise Manager (SQL 7.0 and 2000 supported). - Remote Desktop Password Decoder
Decodes passwords in Remote Desktop Profiles (.RPD files). - PWL Cached Password Decoder
Allows you to view all cached resources and relative passwords in clear text either from locked or unlocked password list files. - Password Crackers
Enables the recovery of clear text passwords scrambled using several hashing or encryption algorithms. All crackers support Dictionary and Brute-Force attacks. - Cryptanalysis attacks
Enables password cracking using the ‘Faster Cryptanalytic time – memory trade off’ method introduced by Philippe Oechslin. This cracking technique uses a set of large tables of pre calculated encrypted passwords, called Rainbow Tables, to improve the trade-off methods known today and to speed up the recovery of clear text passwords. - WEP Cracker
Performs Korek’s WEP Attack on capture 802.11 capture files containing WEP initialization vectors. - Rainbowcrack-online client
Enables password cracking by mean of the outstanding power of this on-line cracking service based on RainbowTable technology. - NT Hash Dumper + Password History Hases (works with Syskey enabled)
Will retrieve the NT password hash from the SAM file regardless of whether Syskey in enabled or not. - Syskey Decoder
Will retrieve the Boot Key used by the SYSKEY utility from the local registry or “off-line” SYSTEM files. - MSCACHE Hashes Dumper
Will retrieve the MSCACHE password hashes stored into the local registry. - Wireless Zero Configuration Password Dumper
Will retrieve the wireless keys stored by Windows Wireless Configuration Service. - Microsoft SQL Server 2000 Password Extractor via ODBC
Connects to an SQL server via ODBC and extracts all users and passwords from the master database. - Oracle Password Extractor via ODBC
Connects to an Oracle server via ODBC and extracts all users and passwords from the database. - MySQL Password Extractor via ODBC
Connects to an MySQL server via ODBC and extracts all users and passwords from the database. - Box Revealer
Shows passwords hidden behind asterisks in password dialog boxes. - RSA SecurID Token Calculator
Can calculate the RSA key given the tokens .ASC file. - Hash Calculator
Produces the hash values of a given text. - TCP/UDP Table Viewer
Shows the state of local ports (like netstat). - TCP/UDP/ICMP Traceroute with DNS resolver and WHOIS client
A improved traceroute that can use TCP, UDP and ICMP protocols and provides whois client capabilities. - Cisco Config Downloader/Uploader (SNMP/TFTP)
Downloads or uploads the configuration file from/to a specified Cisco device (IP or host name) given the SNMP read/write community string.
Abel features
- Remote Console
Provides a remote system shell on the remote machine. - Remote Route Table Manager
Enable to manage the route table of the remote system. - Remote TCP/UDP Table Viewer
Shows the state of local ports (like netstat) on the remote system. - Remote NT Hash Dumper + Password History Hases (works with Syskey enabled)
Will retrieve the NT password hash from the SAM file regardless of whether Syskey in enabled or not; works on the Abel-side. - Remote LSA Secrets Dumper
Dumps the contents of the Local Security Authority Secrets present on the remote system.
Popularity: 39% [?]


 11:39
11:39
 Hacking Skills
Hacking Skills







0 comments:
Post a Comment